MBAM Not BitLocking
MBAM is installed, group policies are set. You install the MBAM client and nothing happens.
From your command prompt run Setspn -s http/<correct url> <serviceaccount>. This will create the correct SPN. Next I deleted the incorrect SPN by running Setspn -d http/<incorrect url> <serviceaccount>. I then listed the SPN again to make sure it all looked ok.
First place to start is the Eventlog. Open eventvwr.msc and browse through to 'Applications
and Services Logs\Microsoft\Windows\MBAM'. In my case I had 'TPM hardware is missing error'
This was an easy one to sort out. Just reboot, enter the BIOS and enable the TPM module. Some manufacturers do offer tools to do this remotely so might be worth checking with your vendors on this one if you have a bunch of machines to do.
Once the machine came back up it still wasn't encrypting the disk so back to the eventlog we go. This time I was presented with 'Unable to connect to the MBAM Recovery and Hardware service. Access was denied by the remote endpoint.'
For this one I started with checking access to the endpoint. To do this open up regedit and browse to 'HKLM\Software\Policies\Microsoft\FVE\MDOPBitLockerManagement'. Copy the value of the KeyRecoveryServicesEndpoint and paste it into a web browser. If you get a 404 page not found or something similar then chances are you have specified the wrong URL in the group policy.
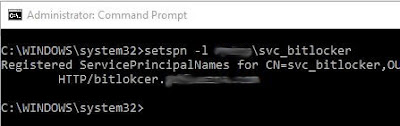
In my case I received an authentication popup. A little bit of research pointed me to check the SPN of the AppPool account. To do this open up a command prompt and enter setspn -l <serviceaccount>.
If you look at the above screenshot you can see that the SPN for HTTP is bitlokcer. This was created when I performed the MBAM install. I fat fingered the url when configuring the website. I went back to the website and changed the bindings to fix it but never changed the SPN. Luckily this isn't to complicated to do.
From your command prompt run Setspn -s http/<correct url> <serviceaccount>. This will create the correct SPN. Next I deleted the incorrect SPN by running Setspn -d http/<incorrect url> <serviceaccount>. I then listed the SPN again to make sure it all looked ok.
Now that the SPN has changed the delegation will need to be updated to reflect the new SPN value. To do this open AD Users and Computers and find the service account. Open the properties and select the Delegation tab, Select 'Trust this user for delegation to specified services only'. Ensure 'Use Kerberous only' is selected. Click Add. Click 'Users or Computers'. Enter the service account name and click OK. Select the new SPN from the list and click OK.
Now that should cover a lot of possible config issues. However for me it still wasn't working. I tried a few more reinstalls, changing the url and removing the need for https. Nothing worked so I logged a ticket with Microsoft and they fixed it in about 20 mins.
The final solution for me. Make sure your DNS entries are A records and not aliases. I had Bitlocker set up as an alias for the server name. As soon as I deleted the alias and set up a standard host record it worked great and I instantly got the below.
As with anything you find on the Internet use this at your own risk. Just because it worked for me doesn't mean it will work for you.







Comments
Post a Comment