Local Administrator Password Solution(LAPS)
We have all come across it. It's a problem as old as the computer itself. Ever since those first few engineers sat around the PC and said, "Hey Frank, I can'y log in. What's the password?" I am of course talking about local admin passwords. For what ever reason your local admin password will eventually leak out and when it does, it spreads quicker than rumors of free donuts in the break room.
You may have combated this with a script that you run once a year that changes the local admin password. The problem with this solution is that if a machine is turned off or remote then it won't get the script run against it. You could put the script into a logon script but then your sticking a clear text version of the script onto your network somewhere.
"Well, I just use GPO to deploy my passwords using Group Policy Preferences." I hear you say. This I will agree was an excellent solution until https://technet.microsoft.com/en-us/library/security/ms14-025.aspx. That's right your hashed password stored in the group policy is hackable. I have tested with a Powershell script and can confirm the password is easily attained, so this is now a bad idea.
Well Microsoft were kind enough to replace that GPO feature for us in something called the Local Administrator Password Solution. It makes use of AD to store the passwords so no extra hardware is required, however the AD Schema will need to be extended to add two (2) attributes and you will need to deploy a client to every machine, which I grant you is annoying. You will also need to configure some settings via GPO....well just one setting if you follow this blog. Once this is done however you will have a random local admin password on every machine you decide to manage. This password is stored in the AD attribute ms-Mcs-AdmPwd and only people who have permission to read this attribute can retrieve the password.
The basics of how this works is that every time group policy is refreshed, which is every 90 minutes-ish by default, the PC will check AD for the ms-Mcs-AdmPwdExpirtationTime. It compares this value to its local time and if this time has passed it will generate a new password, store that password in the ms-Mcs-AdmPwd attribute on its account, then change its local admin password to match. Simple as that. Each machine gets a different password so if one machine is compromised, the whole network isn't at risk.
You can configure the length and complexity of the password as well as specify a different local account name to modify if you don't want to mess with the Administrator account. Out the box it will generate 14 character passwords consisting of Uppercase, Lowercase, Numbers and Symbols. It will do this every 30 days. I should also mention that this tool is free however support is through Microsoft Premier Services.
The steps required to get this thing up and running are:
Launch a Powershell console

Navigate to the machine. Right click it and select Properties.

And that is that. You should now have a fully automated password management solution with zero down and zero monthly payments......support is extra of course.
It also goes with out saying that as with anything you get from the Internet, use the above at your own risk. Just because it worked for me doesn't mean it will work for you.
You may have combated this with a script that you run once a year that changes the local admin password. The problem with this solution is that if a machine is turned off or remote then it won't get the script run against it. You could put the script into a logon script but then your sticking a clear text version of the script onto your network somewhere.
"Well, I just use GPO to deploy my passwords using Group Policy Preferences." I hear you say. This I will agree was an excellent solution until https://technet.microsoft.com/en-us/library/security/ms14-025.aspx. That's right your hashed password stored in the group policy is hackable. I have tested with a Powershell script and can confirm the password is easily attained, so this is now a bad idea.
Well Microsoft were kind enough to replace that GPO feature for us in something called the Local Administrator Password Solution. It makes use of AD to store the passwords so no extra hardware is required, however the AD Schema will need to be extended to add two (2) attributes and you will need to deploy a client to every machine, which I grant you is annoying. You will also need to configure some settings via GPO....well just one setting if you follow this blog. Once this is done however you will have a random local admin password on every machine you decide to manage. This password is stored in the AD attribute ms-Mcs-AdmPwd and only people who have permission to read this attribute can retrieve the password.
The basics of how this works is that every time group policy is refreshed, which is every 90 minutes-ish by default, the PC will check AD for the ms-Mcs-AdmPwdExpirtationTime. It compares this value to its local time and if this time has passed it will generate a new password, store that password in the ms-Mcs-AdmPwd attribute on its account, then change its local admin password to match. Simple as that. Each machine gets a different password so if one machine is compromised, the whole network isn't at risk.
You can configure the length and complexity of the password as well as specify a different local account name to modify if you don't want to mess with the Administrator account. Out the box it will generate 14 character passwords consisting of Uppercase, Lowercase, Numbers and Symbols. It will do this every 30 days. I should also mention that this tool is free however support is through Microsoft Premier Services.
The steps required to get this thing up and running are:
- Install LAPS client on an initial machine
- Use this machine to extend Active Directory Schema
- Check for users with Extented Rights
- Remove Extended Rights for any non approved users.
- Add rights for machines and approved users
- Configure the GPO to Control LAPS behavior
- Deploy the client to all managed workstations
Step 1. Install LAPS Client
Download LAPS.x64.msi and launch it.
Click Next.
Accept License Agreement. Click Next.
Click Management
Tools and select Entire feature will
be installed on local hard drive. Click Next
Click Install
Click Finish
Step 2. Updating the Schema.
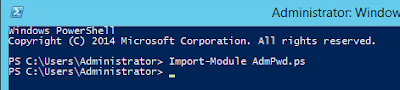
For this make sure you log into the machine with an account that is a member of schema admins. This step will add two (2) attributes to the schema called ms-Mcs-AdmPwd and ms-Mcs-AdmPwdExpirtationTime.Launch a Powershell console
Enter command Import-Module
AdmPwd.ps
Enter Command Update-AdmPwdADSchema
Step 3. Check for users with Extended Rights.
The reason for this step is that the new schema attributes are secured as Extended Rights in AD. As such, we need to ensure no one has Extend Rights granted to them that shouldn't. It's a lot easier than it sounds.
Either use the same Powershell console you used to upgrade the schema or open a new Powershell console and run the command Import-Module AdmPwd.ps.
Enter command Find-AdmPwdExtendedRights
–Identity <Distinguished Name of OU>. The OU is the OU that contains the Workstations or Servers that you are going to manage the passwords for.
The output of this command will list any users with Extended Rights in the ExtendedRightsHolders column. If you see any accounts listed that you don't want to access the passwords make a note and proceed to step 4. We will be removing CORP\TestUser1.
Step 4. Remove Extended Rights.
Launch Active Directory Users and Computers. Navigate to the OU that has the Extended
Rights permission.
Right click the OU and select Properties
Select the Security
Tab and click Advanced
Select the user that has the Extended Rights permission and
click Edit
Remove the check in the All
extended rights box and click OK
Click OK on all remaining boxes to close them and get back to Active Directory Users
and Computers.
Step 5. Adding Extended Rights.
Now that we have all the unneeded rights removed, we need to add permissions so that the machines can modify their own passwords and support personnel can access the passwords to retrieval.
If you still have the Powershell console open use that. If not open another Powershell console and run the command Import-Module AdmPwd.ps.

Enter Command Set-AdmPwdComputerSelfPermission
–Identity <Distinguished Name of OU>. This command will allow the computers to update their own passwords.
Enter Command Set-AdmPwdReadPasswordPermission
–Identity <Distinguished Name of OU> -AllowedPrincipals <Users\Group,User\Group>. This command will grant permission to a person\group the rights to retrieve the password. In the screenshot below, I granted the rights to a group called CORP\Helpdesk_IT.
Enter
Command Set-AdmPwdResetPasswordPermission
–Identity <Distinguished Name of OU> -AllowedPrincipals
<User\Group,User\Group>. This will grant permission to force a password change the next time the machine checks in.
Just repeat the above for any OU that contains machines that you want to manage the passwords for.
Step 6. Configure Group Policy to Control LAPS.
LAPS settings are all controlled via group policy. There are only 4 settings in total and unless you have strict rules dictating your local admin account and passwords, I would recommend just leaving everything alone and only changing one setting as per the instructions below.
Launch the Group Policy Management Console and edit the
policy controlling the in scope machines.
Expand Computer
Configuration\Policies\Administrative Templates\LAPS. Right click Enable local admin password management and click Edit.
Select Enabled and
click OK. Close the Group Policy
Management Editor.
That one setting will tell the clients to start managing their passwords using LAPS. Now all that needs to be done is to deploy the client to all the machines that need to be managed.
Step 7. Deploy Client.
The client to be deployed is the same client that was installed in Step 1. Using that msi you can either install manually or via a script\SCCM deployment using the following command:
msiexec
/i \\server\share\LAPS.x64.msi /quiet.
This assumes you have the msi stored on a network share somewhere.
Once the client is out there your machines will each change there passwords to a random 14 character password containing uppercase, lowercase, numbers and symbols. This change will occur every 30 days.
Retrieving Passwords.
There are 3 main options for retrieving a passwords. They are:
Option 1
On a that has the client installed as per Step 1 go to the start menu and launch LAPS UI
Enter the computer name and click search.
The password will appear in the password box. You can also specify a date for the password
to be changed from here if you want it to reset earlier than its scheduled
expiration time.
If you do not have permissions to view the password for that
machine the Password field will be blank.
Option 2
Launch Active Directory Users and Computers.
Click
on the Attribute Editor tab. Scroll through the list and find ms-Mcs-AdmPwd. The value is the password.
Option 3
From a machine with the LAPS powershell module installed.
Launch Powershell
Enter command Import-Module
AdmPwd.ps

Enter command Get-AdmPwdPassword
–ComputerName <machine name>
And that is that. You should now have a fully automated password management solution with zero down and zero monthly payments......support is extra of course.
It also goes with out saying that as with anything you get from the Internet, use the above at your own risk. Just because it worked for me doesn't mean it will work for you.
























Comments
Post a Comment